Zero Trust Networks
How is the IT world coping up with the remote work era using modern cybersecurity architecture?
Before talking about Zero Trust, what it is, and how companies are implementing it, let us take up an example of an imaginary city.
Hypothetical case
A long time ago, a walled empire known as Talevaria was considered one of the safest and most loved realms of the medieval age. No one outside the kingdom was allowed in, and no one from inside was allowed to go out. People inside were free to move around the confines of the wall without any restrictions, and people from the outside wished they could be a part of the fantastic kingdom. Talevarians had unrestricted access to every resource inside the walls, and there were no law enforcement officers maintaining order because the King trusted his subjects. Kingdom's entire infantry was deployed at the borders, protecting it from the neighboring kingdoms as it was frequently under attack because of the abundance of resources and its strategic importance.

While the brave warriors of this kingdom were busy fighting at the border, an uprising started taking over provinces, one by one. Soon, the entire kingdom was in the hands of these rebels. There was no way to control the situation as all the law enforcement personnel were deployed at the kingdom's border. This case is the classic example of traditional network architecture, and the Zero Trust model can help solve these issues.
Zero Trust Networks

What is it?
The concept of Zero Trust is not new. It was coined in 1994 by Stephen Paul Marsh for his doctoral thesis, but John Kindervag repopularized it in 2010 while working as a researcher at Forrester Research. Although it appeared to be an overkill back then, it makes more sense now than it ever did before. There are many definitions of Zero Trust on the internet, but the one from TechTarget made the most sense:
It is a security framework that fortifies the enterprise by removing implicit trust and enforcing strict user and device authentication throughout the network.
So, in simple terms, the Zero Trust model promotes the need to verify every device that connects a private network, irrespective of their location, be it inside a secured perimeter, or outside, from a remote location, or the device state. In pre-pandemic times, the traditional model required every resource that the organization needed to be within the 'protected boundaries' of the network. However, in present times, that is not possible. With more than half of the workforce working remotely, this model fails catastrophically. It was easier for cybersecurity professionals when pre-configured devices were provided to employees. Nevertheless, this option was heavier on the company's pocket. The introduction of the BYOD (bring-your-own-devices) system has become more challenging for them to maintain order on the network. The users' device settings could change (or be intentionally changed), could be affected with malware, or compromised by an attacker, which could leave the network vulnerable. What if the company uses resources that are scattered all over the internet. With the increase in the importance and volume of data, small and medium enterprises opt for cloud services like AWS, GCP, or Azure. This model does not sit well with the traditional on-premise model as the internal network requests these cloud servers for resources. Alternatively, consider this- with more than 50% of the workforce working from their homes, it is not practically possible to check every connection for vulnerability. What if I tell you that Zero Trust solves these issues. By default, Zero Trust bears the motto, "Never trust, always verify." You read that right. No one is trusted, be it the CEO's device, the CTO's, or even the CISO's. Zero Trust takes a hostile approach towards security. Whenever a device is connected to the network, it is allegedly hostile. Username and password authentication are not enough. With Zero Trust, enterprises are bidding goodbye to password-based authentications. Multi-level authorization is required, but that is not it. Here is where it gets interesting.
For example, Emiko is an employee in a multinational tech company living in Tokyo. She had to shift to the WFH model because of the pandemic. Every working day, she uses VPN software to log in to her company's network through her company allotted device. Then, SSH into a system to monitor its status and spends some time doing that. After that, she opens the local storage server to view the last documentation she edited and continues working on it for the remainder of the day. Emiko also has a habit of logging out of each resource she uses on the network. She does not wait for the auto-logout period. Finally, she disconnects the VPN connection when it is time to wrap up. This is Emiko's normal behavior, and the Zero-Trust implemented network knows it. Let us say that Emiko visits her parents in Nakagawa for a weekend and decides to stay there for longer. On Monday, Emiko tried to log in to her VPN account, but apart from the usual login procedure, she had to go through an additional step of entering a one-time password sent to her work email. Only then was she allowed to enter the network. Take another example: Emir works remotely from Istanbul for the same company and has been doing that since the pandemic. Everything seems to be normal until he decides to dual-boot his PC. He logs in normally when the work-day starts, but he cannot log in. Every time he tries to log in, he gets the same alert, Access denied due to policy violation, on each try. Zero Trust would be responsible for this behavior. It already does not trust anyone, but the moment there is some suspicious behavior, it lets its guards up. If you noticed, in the first scenario, the authentication is taken to one additional step when Emiko tries to log in from a new location because the network has never received a login request from that location from Emiko's device. The company can also enforce verifying her before accessing any resource she usually uses. Similarly, when Emir decided to dual boot his PC, he might have turned off Secure Boot in his BIOS to install that Linux OS or maybe changed the boot device order so he could boot from a USB device. So, if the company's policy is that no one with Secure Boot turned off can log in to the network, Emir's device failed to comply with the application policy set by the company, and thus, was not allowed to log in.
Why is it important?
The Covid pandemic pushed almost every tech company out there to move to a remote model. Employees use VPN to get inside their company's network to access data and resources. Nevertheless, the question arises, is that enough? Sure, it is an excellent solution as long as the number of people using it simultaneously can be counted on the fingers. However, what if the number of people using it is in the hundreds? That is a security disaster. Here is where Zero Trust comes to the rescue.

Zero Trust is not some software or even an algorithm that can be added to a network. It is much more complex than that. Imagine you know how every employee in your organization accesses your network. You know what device they use, the OS they use, kernel and its version, BIOS version and settings, kind of software installed, how fast they type, where they usually access the network from, and much more similar stuff. How do you use this information? You match the collected sample with the live session whenever they try to log in. If anything changes, you challenge the employee with more authentication steps or block them altogether. This is how the network gives you access. But is that all that Zero Trust is about? No. One more essential feature is that it only gives you access to the resources you essentially need - nothing more, nothing less. Let's say you have been tasked with reviewing documentation for a new software the company is about to release. Hence, the access you will get is to access the file server with only read and comment privileges. You can neither make changes nor download the file to your local system. When an organization migrates to the Zero Trust architecture, the following advantages can be observed:
- Reduces organizational risk: Zero Trust assumes that all applications and services are malicious and are disallowed from communicating until they can be verified. Thus, it reduces risk because it tracks the communication between these assets.
- Reduce the risk of data breach: Because Zero Trust is based on the principle of least privilege, any user in the system will have to prove identity multiple times for every level of access. There is no ability to access the system laterally due to restrictions in the architecture; therefore, even if the attackers gain access to one segment in the network, there is nowhere they can go from there without establishing trust again. Even for an inside actor, the access would be only limited to the task they are assigned with. No one enjoys unlimited access in Zero Trust architecture.
- Secures cloud adoption: Cloud has become very important for enterprises because they help save capital on infrastructure setup. But cybersecurity specialists dread it because they will not be able to have visibility and access control. However, Zero Trust enables the classification of all assets on the cloud to establish the proper protection and access controls.
- Support regulatory compliance: Regulatory compliance like the GDPR, HIPAA, CCPA, or various other compliance regulations are the top concern for organizations. In Zero Trust, identity and payload are verified each time, stopping the data before the attacker reaches the data. This exceeds the compliance requirements of today's regulatory frameworks.
- Lowers reliance on endpoint protection: Endpoints like servers, laptops, desktops, and Point of Sales (POS) devices are frequently targeted by hackers to gain access to internal networks of an organization. Ransomware and malware also find their way into the network through these endpoints. Organizations spend enough capital on protecting these endpoints, but with Zero Trust, reliance on traditional endpoint protection solutions can be avoided with identity at the center of the network security.
- Enables hybrid workforce security: Rapid adoption of remote working style has forced companies to collaborate from anywhere using any device. Zero Trust enables real-time security across all security domains for this scattered workforce.
Key Principles
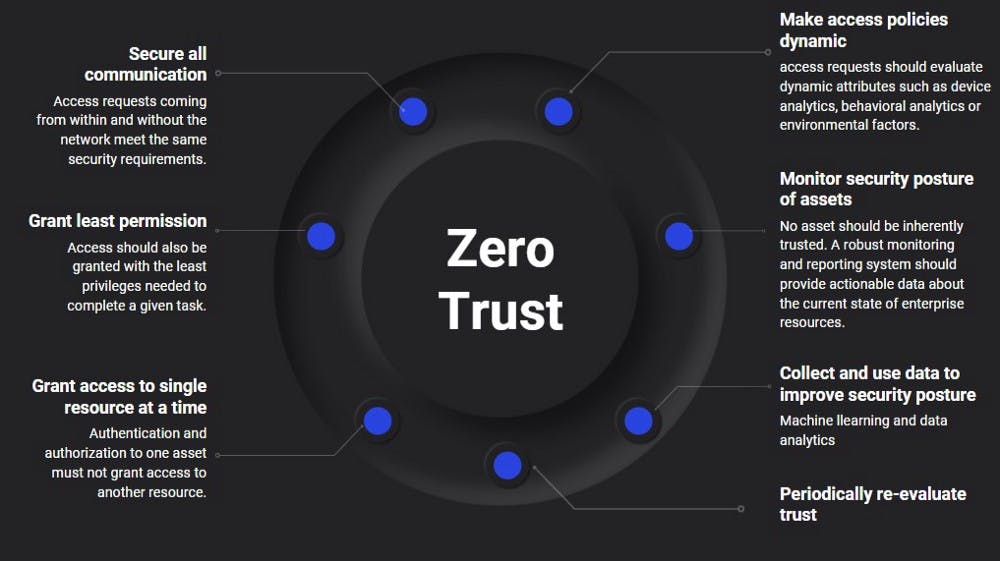
Zero Trust's key feature is least-privileged access, which assumes that no user or application should be inherently trusted. This is the very basics of Zero Trust, but the fundamental principles are as follows:
- Secure all communication: Access requests, be in form within the network or beyond it, should meet the same security requirement. No one gets more privilege.
- Grant least privilege: Access should be given the least privilege to complete a given task. We talked about this earlier when I mentioned the permission needed to review a documentation is read and comment. You don't need any more permissions for reviewing.
- Grant access to a single resource at a time: When a user authenticates, they are only authorized for a single asset. If they need to use another resource, they'll need to get authenticated again.
- Make access policies dynamic: Authenticating a user should not depend solely on credentials and static policies. Policies should be dynamic. Policies can take into consideration device analytics, the behavior of the user, or even environmental factors. For example, it could depend on the BIOS settings of the device, the device's location, the charge available on the device, the typing speed of the user in the current session, malware infection, etc.
- Monitor security posture for assets: As a security professional, you'll need to monitor activities like web tampering, suspicious processes, web shells, unusual logons, and other malicious processes in real-time to take action against them immediately.
- Collect and use data to improve security posture: This includes collecting data about user behavior, device status, and location to optimize the authentication service using machine learning.
- Periodically re-evaluate trust: Once in a while, the trust should be re-evaluated to make sure everything is in order and if some resource needs more level of protection than it did before.
How to apply?
Zero trust might be fascinating in theory, but how do enterprises apply it to their network? In order to establish Zero Trust, one needs to monitor and control the users constantly and the traffic of the network, verify the traffic between any two points in the network and club it with strong multifactor authentication methods such as biometrics or one-time codes.
- Identify protected resources: Before implementing Zero Trust architecture, assets, data, and services need to be classified. You need to determine what you will be protecting on priority.
- Define policies: Next, the user's expected behavior should be documented. This step can be accomplished by asking the questions: "Who is going access what, when and why, and from where?"
- Identify data feeds: For implementing this step, we can break it down to a straightforward question: "What sort of data do you need to make the access generating decision?" The data feed could include threat intelligence, activity logs, compliance systems, etc.
- Devise the Trust Algorithm: This algorithm will grant access based on factors like the request, policy, and the data feed. This will also evaluate the behavioral patterns to make access-granting decisions.
- Define architecture: This usually is dependent on the organization's current setup. The architecture will map the monitoring, accessing, and all other aspects of how the network will operate.
Industry Adoption
Even though Zero Trust architecture is a widely recognized way to mitigate intrusion, its adoption has been slow and inconsistent. A study by IBM in 2021 showed that The average cost of a breach was USD 1.76 million less at organizations with a mature zero-trust approach, compared to organizations without zero trust. Of all the organizations that have started implementing it, most of them are still in an intermediate phase. The survey by IBM revealed that 35% of the participating organizations had partially or fully deployed the Zero Trust model, and of the remaining 65%, 22% were planning to deploy it within a year.
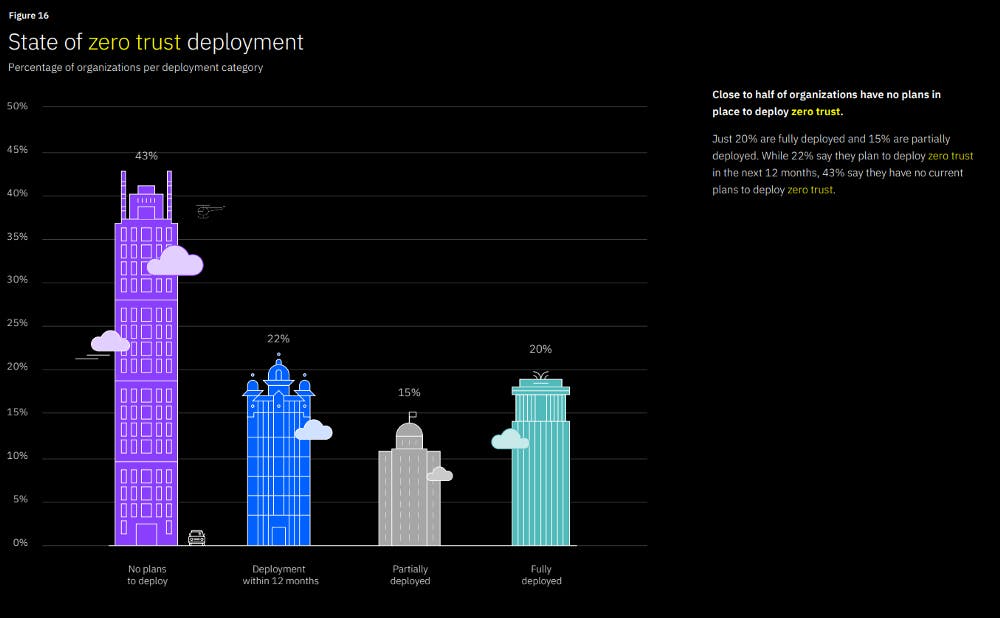
It also stated that $5.04m was the average cost of a breach at organizations without zero trust deployed. It is also true that about 43% of organizations have no plans of implementing Zero Trust. In May 2021, the Biden administration instructed US Federal agencies to adhere to NIST 800–207 standard for Zero Trust because of the increasing number of high-profile security breaches. As a result, this standard has been subjected to validation and suggestions from various private and government organizations. Hence, it is the go-to standard for private enterprises.
Closing Notes
Zero Trust is a new way to architect an organization's cyber defense. It provides a collection of concepts, ideas, and component relationships designed to eliminate the uncertainty in enforcing accurate access decisions in information systems and services. Zero Trust's benefits outweigh its implementation cost and any other factors.
