To answer this question, let's go back to May 12th, 2017. Computers of the hospitals across London were stuck on a red screen which said,
"Oops, your files have been encrypted. Send $300 worth of Bitcoins to this address."
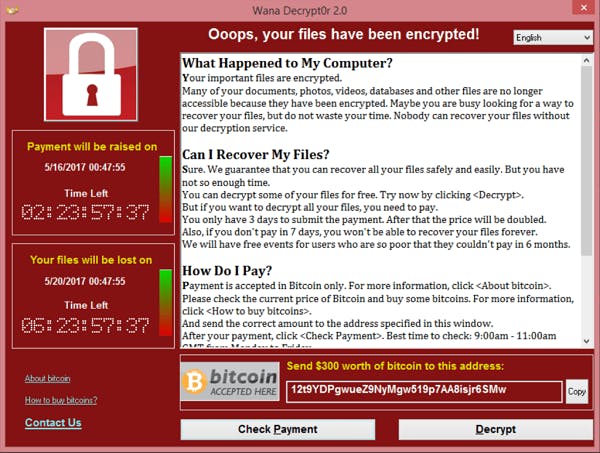 The dialog box also had a timer that indicated when the price would increase, followed by a deadline after which the files could no longer be retrieved.
The dialog box also had a timer that indicated when the price would increase, followed by a deadline after which the files could no longer be retrieved.
What is Ransomware?
The idea behind Ransomware is quite simple. If your files are encrypted, and you don't have the key to decrypt them, your files are no longer readable. You can take, for example, the BitLocker feature on Windows. When you encrypt your drive, you set a passphrase for it. If you forget your code, you no longer have access to your files. The same principle is applied to Ransomware. Only, this time, someone else does it to your files without your permission and demands a ransom in return for the key.
The WanaCrypt
This Ransomware attacking hospitals in London was called Wanacrypt, but people quickly started calling it Wannacry.
The United Kingdom National Health Service or NHS had to cancel 6912 appointments, with 45 hospitals being affected. The patient registration system was not functional, the inter-department communication was broken, hospitals had to deploy runners to grab reports from various departments manually, and procedures that required high-tech interventions were suspended. There was panic all over, and hospitals began going old-fashioned, using pen and paper.

WannaCry was targeting Windows computers, specifically the ones that were connected to the network. But, if you think, all computers within a hospital should come under a network. But the thing is, not all computers are connected, partly for this exact reason. Systems like CT Scanner were kept isolated and not connected to the network. Affected hospitals were relying on these standalone machines to carry out their work.
But were only hospitals the target?
 Simultaneously, over 100 countries had been affected by this Ransomware, but the attack was not focused on healthcare systems. It was only the United Kingdom, where healthcare systems were particularly affected.
Simultaneously, over 100 countries had been affected by this Ransomware, but the attack was not focused on healthcare systems. It was only the United Kingdom, where healthcare systems were particularly affected.
Let's time travel
Now, before we proceed, let's travel further back in time. This sub-story might seem completely unrelated, but it is very related.
Someone from within the NSA leaked it's ANT catalog, short for Advanced Network Technology catalog, to a journalist (find the file here. Inside this catalog is a list of hacks, available exploits, and surveillance devices that the NSA can use for any mission. You select an attack that you want to carry out, get the necessary tools issued, and then proceed with the attack.

- Out of all the tools in the catalog, one device was the CottonMouse. It looks like a typical USB plug, completely harmless. But in fact, when connected to the target device, it is wirelessly transmitting all the data flowing through it. Mouse clicks, keyboard strokes, external webcam data, all data is being transmitted to someone as close as the room next door. The NSA created this hardware, and it still isn't available commercially. The catalog even lists its price as $20000. Can you believe it? How powerful can this device be?
- Another device called JETPLOW is an implant that could provide you backdoor access to cisco firewalls.
- Another interesting tool is called RageMaster, an extension to a VGA port. When connected, it can wirelessly transmit everything the VGA adapter on the target machine sees, essentially cloning your screen. Crazy, isn't it?
The devices in this catalog were intended to be used by the TAO, short for Tailored Access Operations. It is a unit within the NSA with the primary objective of target reconnaissance. TAO is the NSA's elite hacking group. They changed their names to Computer Network Operations.
When security firms research hacking campaigns, they usually give hackers units a unique code name. For example, the Russians are called the Fancy Bear, Iranian hackers were called Charming Kitten, and hackers from NSA are called The Equation Group. It is believed that whoever is doing work for the equation group is working in the TAO.
Now, the important part of this story occurs in August 2016. A Twitter feed posted by an account by the name of theshadowbrokers included a link to Pastebin that had the following text along with some pictures.
!!! Attention government sponsors of cyber warfare and those who profit from it !!!! How much you pay for enemies cyber weapons? Not malware you find in networks. Both sides, RAT + LP, full state sponsor tool set? We find cyber weapons made by creators of stuxnet, duqu, flame. Kaspersky calls Equation Group. We follow Equation Group traffic. We find Equation Group source range. We hack Equation Group. We find many many Equation Group cyber weapons. You see pictures. We give you some Equation Group files free, you see. This is good proof no? You enjoy!!! You break many things. You find many intrusions. You write many words. But not all, we are auction the best files.
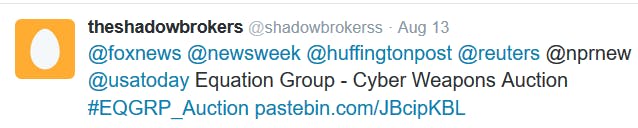 Find the Pastebin archive here.
Find the Pastebin archive here.
This was not a joke. A few files, in fact, had been published on GitHub (now removed). People were looking at it, forking it. The uploaded malware was an exploit for Cisco and Fortinet firewalls. This exploit allowed the attacker to send an exploit to a fully patched firewall and will enable the hacker to take full control.
For the rest of the files, the auction only received $937, which was a big disappointment to the Shadow Brokers. The second dump by the ShadowBrokers was a list of IP addresses that the NAS had infected or were using as a proxy to carry out cyber attacks. It maybe was a way through which the Shadow Brokers wanted to tell the people what they were serious about the files.
Finally, in January 2017, ShadowBrokers made another post saying goodbye. The post said that they could not accumulate the number of bitcoins they were hoping for, so they would release more tools, for free, for everyone to see. They posted around 60 windows executables, link libraries, and drivers, claiming they were developed by the TAO and were exploiting Windows PCs.
But this wasn't the last we heard from the shadow brokers. About three months later, they showed back up in the first week of April, dumping more files for the world to see, along with a message for the President of the United States, saying,
"Respectfully, what the fuck are you doing? TheShadowBrokers voted for you. TheShadowBrokers supports you. TheShadowBrokers is losing faith in you. Mr. Trump helping theshadowbrokers, helping you. Is appearing you are abandoning “your base”, “the movement”, and the peoples who getting you elected.'
This dump contained EternalBlue and EternalRomance. What's unique about EternalBlue is that it can remotely access Windows PCs running SMB, installed by default on all windows machines before windows 8. But here's the interesting thing. Just before a month before shadow brokers had published EternalBlue, Microsoft had patched it. Rumors had it that the NSA had given Microsoft a very quiet heads up about its system's vulnerabilities, telling them that this might be in an upcoming dump.
Back to 2017
When a cyber-attack of this scale breaks into the world, it attracts many security researchers, anti-virus companies, and threat-detection systems. Everyone is in the race to be the first one to find a fix to the problem. You have to understand that when some new threats open up to the world, there are no news pages, no blog posts, or articles about it. It's a strange time where no one knows what's happening. Everyone is talking, tweeting, and sharing screenshots, but there is no clear sense of what is actually going on. Every researcher is trying to get samples of the malware to find a cure, be it huge companies or independent researchers. Among others was a French Security Researcher named Matt Suiche. He was working on finding a fix to this Ransomware. One thing to note is that malware like this is pre-compiled, meaning if you look at the program itself, it's gibberish. It's machine code, not readable by humans. Security researchers use reverse engineer tools like Ghidra or Binary Ninja to convert it to assembly language. Now, this is readable but is very elementary. There are no if-else statements in assembly language. This low level of language requires a lot of skills to make sense of it. While reverse-engineering the malware, Matt noticed something interesting. The malware was using, wait for it, EternalBlue to gain access to PCs released just a month before by the ShadowBrokers. This Ransomware was a self-propagating one, meaning, once it infects a computer, it will try to infect every other computer on the network.
At the same time, another security researcher named Marcus Hutchins was looking at the malware and saw something that is very unusual for a Ransomware. He found that the malware tries to go to a specific 40 characters long URL upon infecting a computer. Wannacry would check if that URL exists, and if it did, it would stop running immediately. It won't propagate, it won't encrypt, it would just halt. Whoever created the Ransomware wanted a functional stop button. Markus checked if the URL was registered, and to his surprise, it wasn't. Strange, the creator forgot to register the domain. He quickly bought that domain name and single-handedly ended the Wannacry panic. No more new computers were getting infected.
A few days after that, a new variant of WannaCry appeared. Matt immediately started working on this. He thought that to make the Ransomware functional again, the creator would just have to change the killswitch URL for the malware, and he was correct. He registered the domain. As a result, not many machines were infected. A few days later, another variant was released, and this time, Checkpoint Software technologies registered the domain quickly, and not many systems were infected by this version either. And then, a fourth variant showed up, and this time, it did not have a killswitch. This version had the potential of ripping through millions of computers worldwide, but this malware never caught the flow. Maybe it wasn't effective, or anti-virus companies had already detected it and put out signatures for it, or people had already updated their PCs.
Who was held responsible?
The US Department of Justice issued a press release where they held a North Korean computer programmer, Park Jin Hyok, responsible for the cyberattack on Sony Pictures, the Bangladesh bank heist, and creating the WannaCry Ransomware. The FBI put him up on the cyber's top 10 most wanted criminals.

But, wait a minute. Bear with me for some more time. As people investigated it further, they found out that there were earlier versions of wannacry which weren't effective because they were not using EternalBlue, because it hadn't been released yet. But on May 9th, 2017, a company called RiskSense published a proof of concept using EternalBlue as an exploit, including source code, and explained how to use it. Three days later, a new version of wannacry with EternalBlue was released, and it used the same code from the blog post.
So does this mean that we can point fingers at RiskSense?
Okay, let's compare the facts.
North Korea pulled the trigger on WannaCry, but they may not have done it if they hadn't seen the blog post by RiskSense, but RiskSense may not have written that blog post if it wasn't for the ShadowBrokers dumping those stolen files to the public, which they wouldn't have done if NSA hadn't developed those exploits, to begin with, but EternalBlue would have never existed if Microsoft had caught the bug during development and testing.
Well, that is a long blame game, and I will leave it to you to decide who to hold responsible.
Thanks
Thanks for reading this article. Also check out my Instagram and Facebook pages for more content.


